Monitor for threats in ConnectWise Automate (On-Prem)
Wouldn’t it be great if you could easily monitor ConnectWise Automate for threats? The Perch community sure thought so. So, we asked the birds in the lab to look into it and rustle something up, and now it’s here.
This new product comes right off the heels of a CW Automate vulnerability (CVE-2020-14159) that led to some Managed Service Providers (MSPs) getting buffalo jumped.
Perch first sounded the alarm on buffalo jumping in the 2020 MSP Threat Report earlier this year. We defined a buffalo jump as an incident where an MSP is compromised for access to multiple customers. A buffalo jump ends with most of your customers being ransomed. You could consider a buffalo jump as a supply chain attack, but at scale.
The U.S. Secret Service even recently jumped into the fray with a warning about hackers targeting MSPs for their wealth of client access.
With hackers showing they understand the value of targeting MSPs, ConnectWise MSPs need to monitor their Automate servers closer than ever. However, they’re notoriously difficult to guard. The logs don’t contain all the audit data defenders need to monitor ConnectWise Automate for threats.
That’s where Perch’s CW Automate advanced monitoring comes in.
What to monitor for
During our initial research, the Perch team discovered a few critical audit points to monitor in your on-premise Automate server. Let’s take a look and noodle some of the threat scenarios for which you’ll now be able to monitor:
Authentication
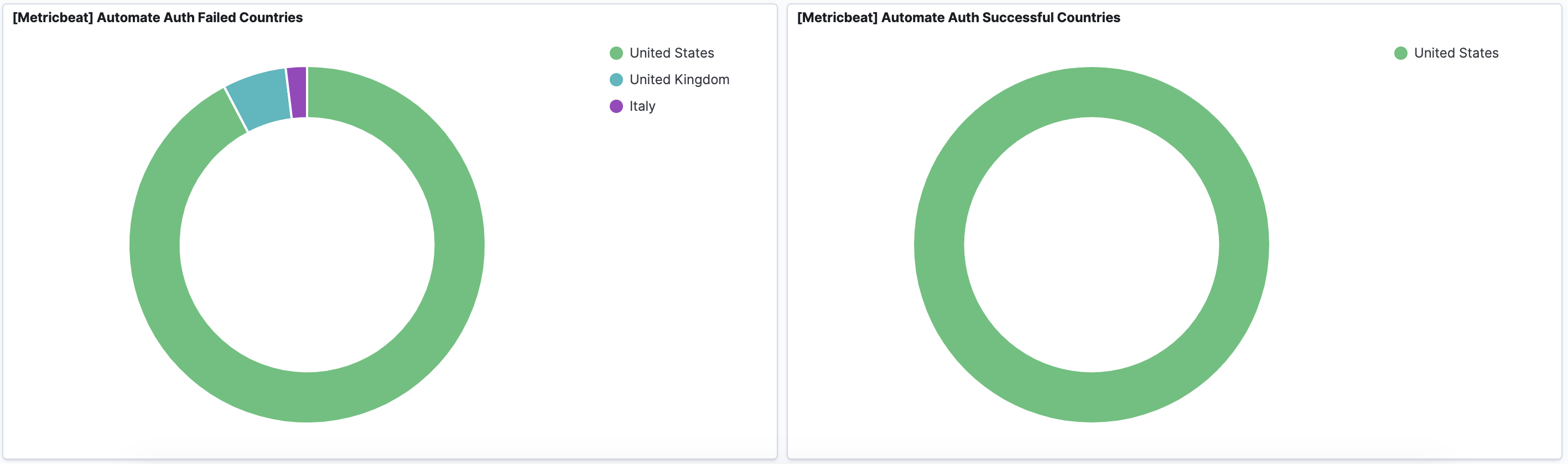
If a hacker authenticates to your Automate server and accesses your client networks, it’s game over. Monitoring authentication to your Automate server is critical.
With Perch, you’ll now be able to monitor for:
- Brute-force attacks
- Successful logins from previously unseen IPs or countries
- Account lockouts
- Failed logins for non-existent users
Actions/Commands
These are audit logs that should be monitored carefully. Threat actors targeting MSPs are known to use RMM tools to command agents. You can find evidence of script and command activity inside of the ConnectWise Automate database.
With Perch, you’ll now be able to monitor for:
- Brute-force attacks
- Successful logins from previously unseen IPs or countries
- Account lockouts
- Failed logins for non-existent users
Actions/Commands
These are audit logs that should be monitored carefully. Threat actors targeting MSPs are known to use RMM tools to command agents. You can find evidence of script and command activity inside of the ConnectWise Automate database.
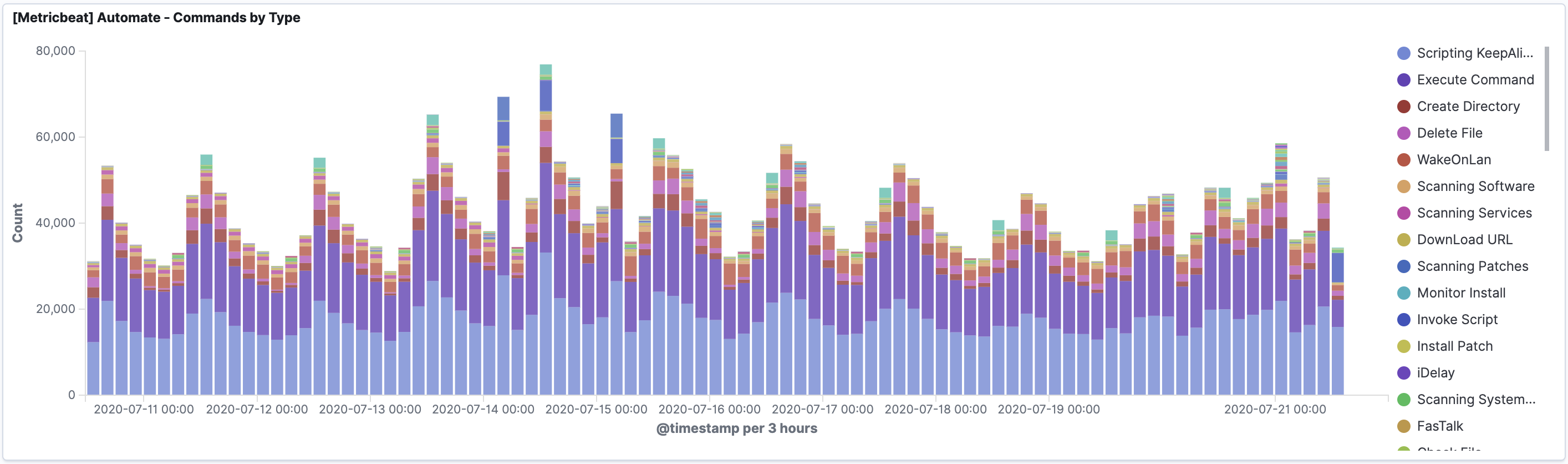
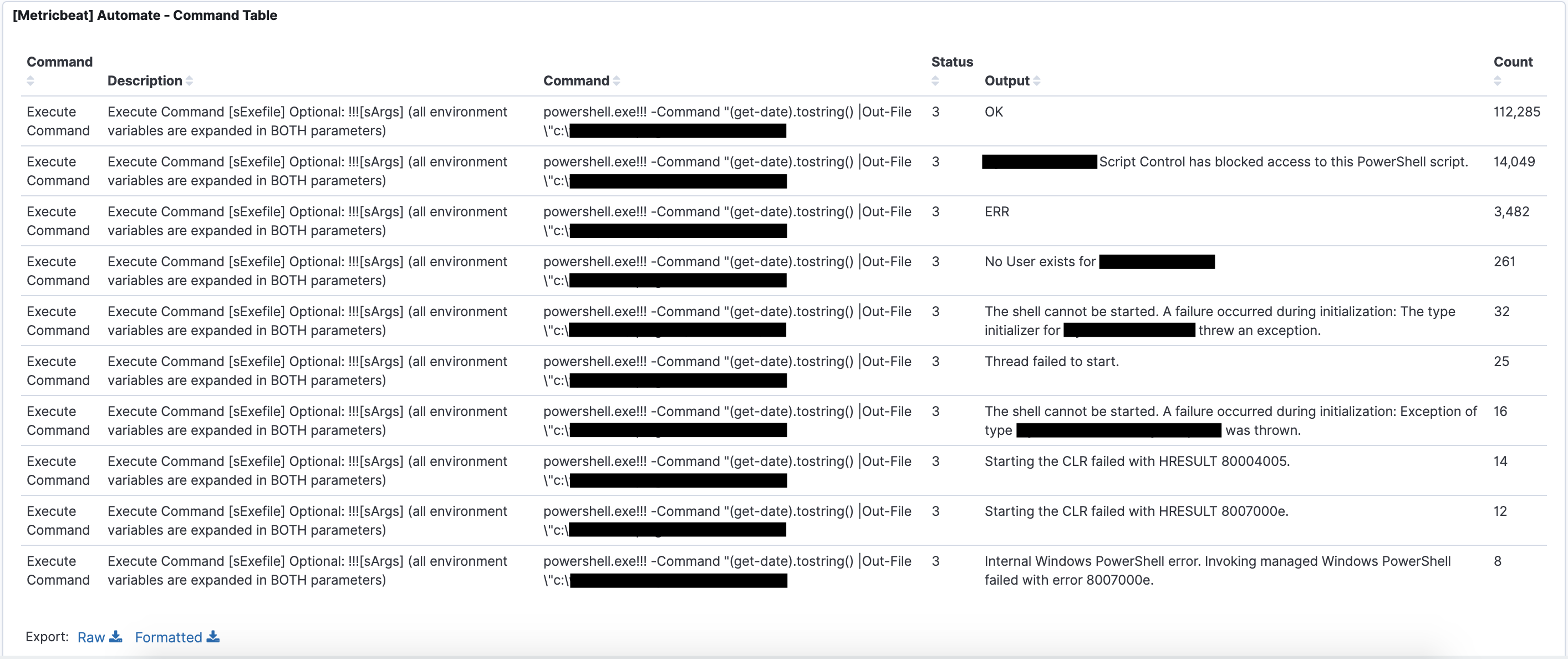
You can now monitor for:
- New scripts or commands being executed
- Mass file downloads by agents or a spike in file downloads
- Spikes in commands or scripts running executables on client computers
- Spikes in script creation
- Accessing/downloading files on client computers
Computers
Automate agents collect valuable data about the computers managed by your MSP. Any data that’s in your computer details can be reported or alerted on.
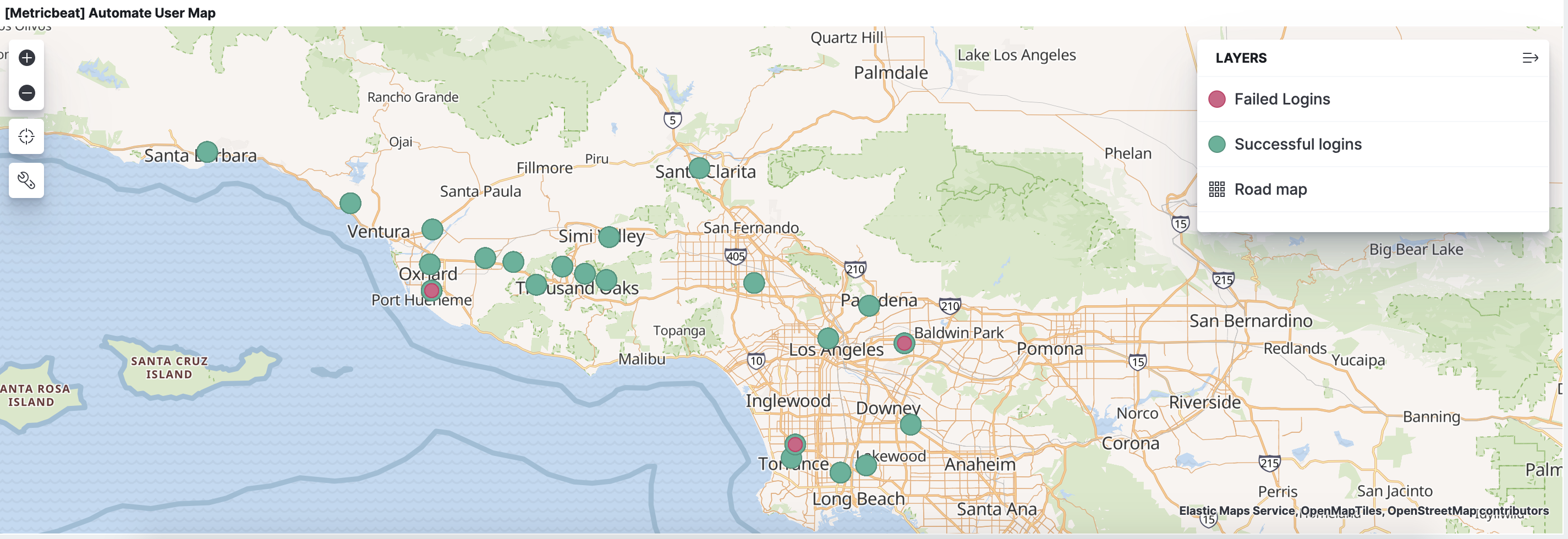
Agents have authenticated access to the Automate server, which opens up the attack surface on your server. That’s exactly what we saw in CVE-2020-14159. One of the ConnectWise remediation steps for that vulnerability was to audit your Agents for locations you don’t recognize and remove those agents.
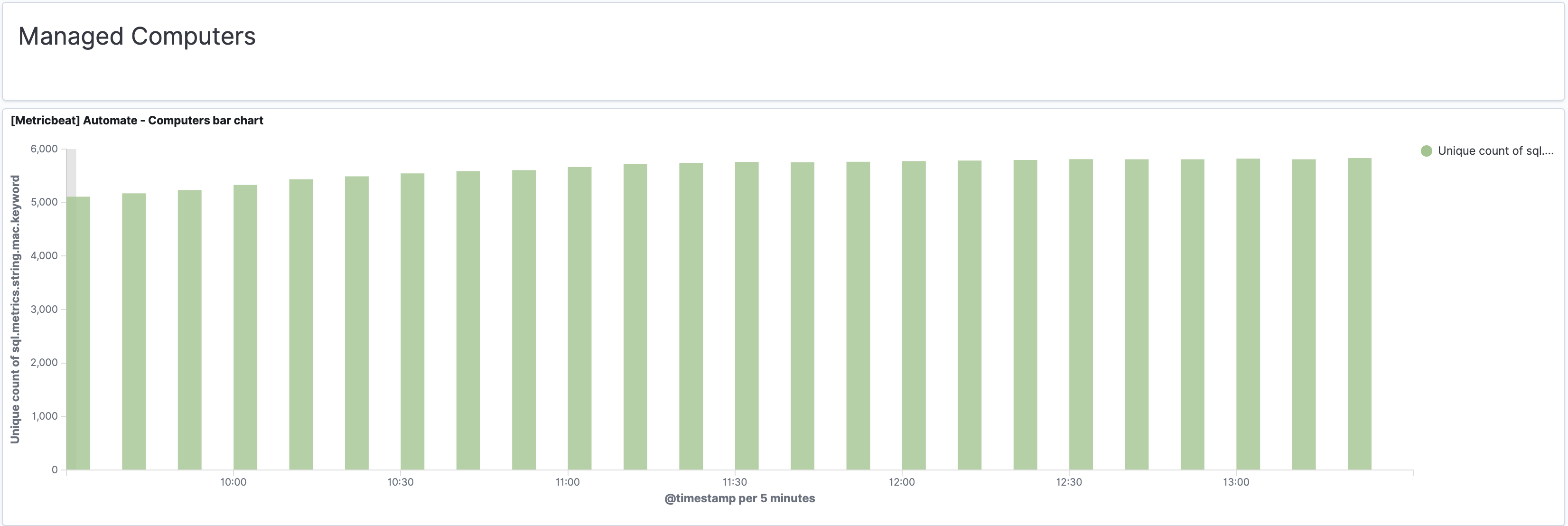
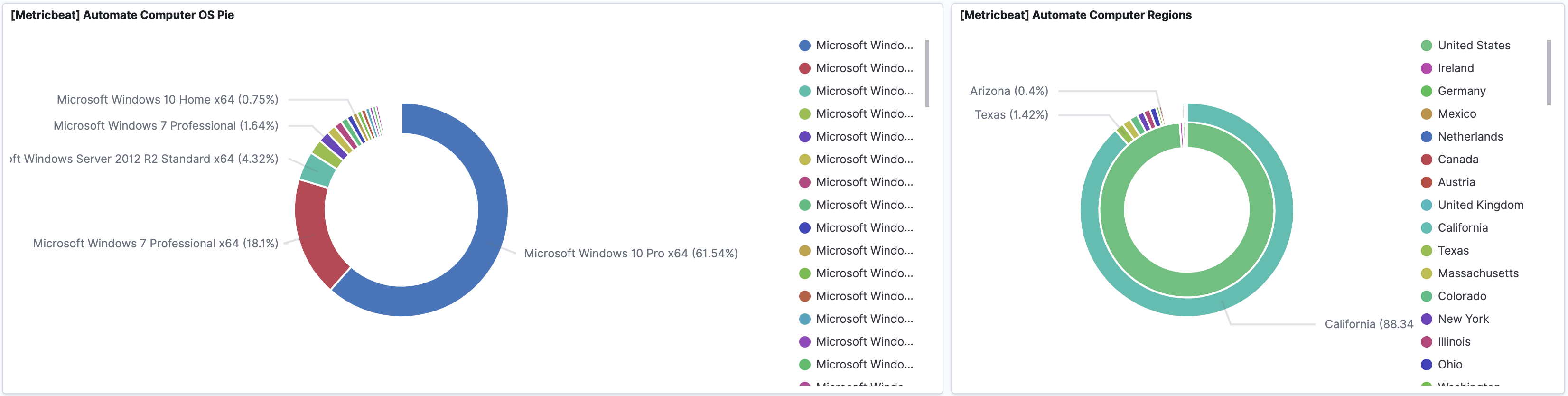
With Perch, you can aggregate data across multiple Automate servers into a single report. All report scopes can be as narrow as a single server and client, or as broad as all clients on all Automate servers. This is vital for people monitoring multiple Automate servers.
With this new product, you’ll be able to monitor for:
- New Agents from unexpected locations
Software/Services/Auto Startups
Automate Agents also collect software, service, and startup script info from computers. Even if clients are not subscribed to Perch, Perch’s 24/7 SOC can find an incident from these computer records as you’re using Perch to protect your house.
You’ll be able to monitor for:
- New and uncommon software installations
- Unapproved software installation
- Uncommon services being installed or started
- AV & EDR services being stopped
- New persistence mechanisms implanted
Get CW Automate monitoring
As with Perch’s other cloud integrations, you’ll now be able to monitor your Automate servers in real-time. We’ve created saved searches, visualizations, dashboards, and event notifications to cover all the possible scenarios above.
To learn more about how Perch can monitor your on-prem ConnectWise Automate, go here.


